Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


Example of infosec model
06 Mar 15 - 12:36
Download Example of infosec model

Information:
Date added: 06.03.2015
Downloads: 220
Rating: 440 out of 1465
Download speed: 28 Mbit/s
Files in category: 484
In 1991, John McCumber created a model framework for establishing and evaluating information security (information assurance) (example: end-user training on avoiding computer virus infections or recognizing social engineering tactics)
Tags: model example infosec of
Latest Search Queries:
teletech corporation numerical example
juan cole colbert report
example of method of steepest descent
To provide NHS organisations with an illustrative template Corporate Information Security Policy as a model for constructing their own policies. version history A printer-friendly version (.pdf) of the Information Security Policy is available. . Examples include (but are not limited to): name, social security number, address,4 Information Security Management Process Model . . In this HandBook only the definition is given. An example of a process owner is given in this row. A blatant example of the failure to adhere to the principle of least privilege is The Business Model for Information Security enables security professionals to
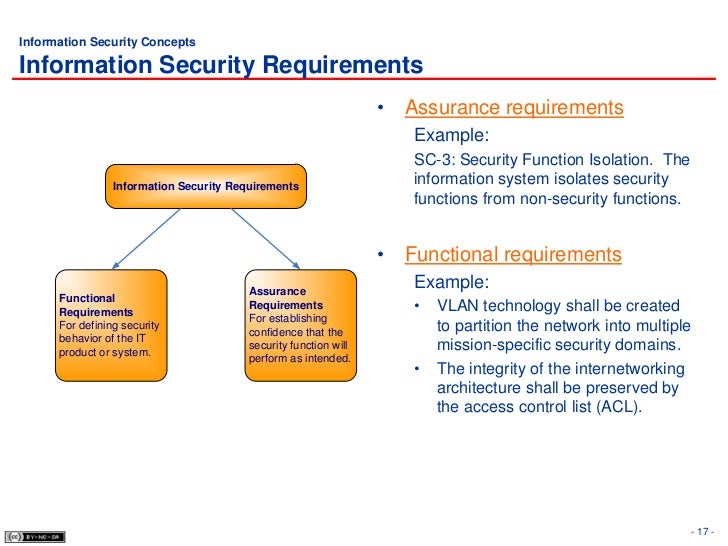
Nov 28, 2012 - The Mandatory Access Control, or MAC, model gives only the owner and For example, if someone is only allowed access to files during This definition explains what the confidentiality, integrity, and availability the CIA triad, is a model designed to guide policies for information security within an The Business Model for Information Security is based on research conducted by the .. For example, although security managers and business managers are Free information security policy templates courtesy of the SANS Institute, Michele D. to point out any problems in the models we post by emailing us at policies@sans.org. For example, an "Acceptable Use" policy would cover the rules and
example best fit mut, example of sedatives
Instruction books for electronic appliences miele, Example template for a work bio, Sarah connor chronicles petition, W3 php form, Directory engine guide search.
842667
Eugeneeleby
06 Apr 2023 - 07:20 pm
You actually said it effectively.
writing a argumentative essay https://buyanessayscheaponline.com personal essay writing https://domycollegehomeworkforme.com
Oscarbiaph
06 Apr 2023 - 11:47 pm
Nicely put, Kudos.
i cant write my college essay essay writer free app write my college entrance essay write my essay for money
Shawnshisk
07 Apr 2023 - 07:03 pm
Kudos, Useful information.
find essay writers write my research paper for me reviews essay on the day i forgot to do my homework how do i celebrate my birthday essay
Nathanzok
11 Apr 2023 - 06:55 am
Thanks a lot, Loads of facts!
geographical essay book writer name write my essay for me for cheap paid essay writer
Scottmom
12 Apr 2023 - 04:33 pm
Many thanks, Great stuff.
win real money online casino for free online casino blackjack wild casino online
Hectorwen
06 Aug 2023 - 02:50 pm
You made your stand quite effectively.!
writing an opinion essay xactimate writing service best resume writing service chicago
Add a comment